Users & Security
Teams and User Roles
Cronitor's team management lets you invite colleagues, assign appropriate permissions, and configure enterprise authentication. Control who can view, edit, or manage your monitoring infrastructure with flexible user roles.
User Roles
Cronitor uses three user roles to control access to your monitoring resources. Each role builds on the permissions of the previous one:
| Role | Description | Best For |
|---|---|---|
| Read-only | View-only access to monitors, dashboards, incidents, and telemetry data. Cannot create, edit, or manage any resources. | Stakeholders, executives, and external consultants |
| User | Create and manage monitors, status pages, incidents, alerts, integrations, and API keys. Cannot access team settings or billing. | Engineers, DevOps teams, and day-to-day operators |
| Administrator | Full access including team member management, role assignment, billing, and SAML SSO configuration. | Team leads, managers, and IT administrators |
Managing Your Team
Accessing Team Settings
Navigate to Team Settings from your account menu. You'll need Administrator permissions to access this page.
Adding Team Members
Invite New Team Members
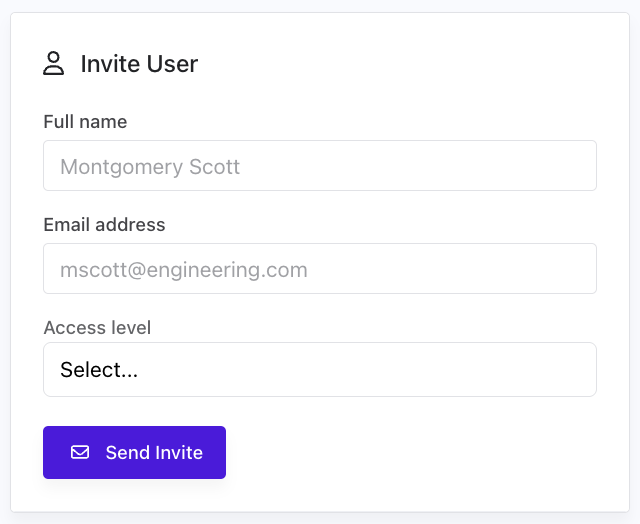
- Click "Invite User" in your Team Settings
- Enter their email address
- Select their role (Read-only, User, or Administrator)
- Click "Send Invitation"
The new team member will receive an email invitation to join your Cronitor organization. They can accept the invitation even if they don't have a Cronitor account yet.
Changing User Roles
Managing User Roles
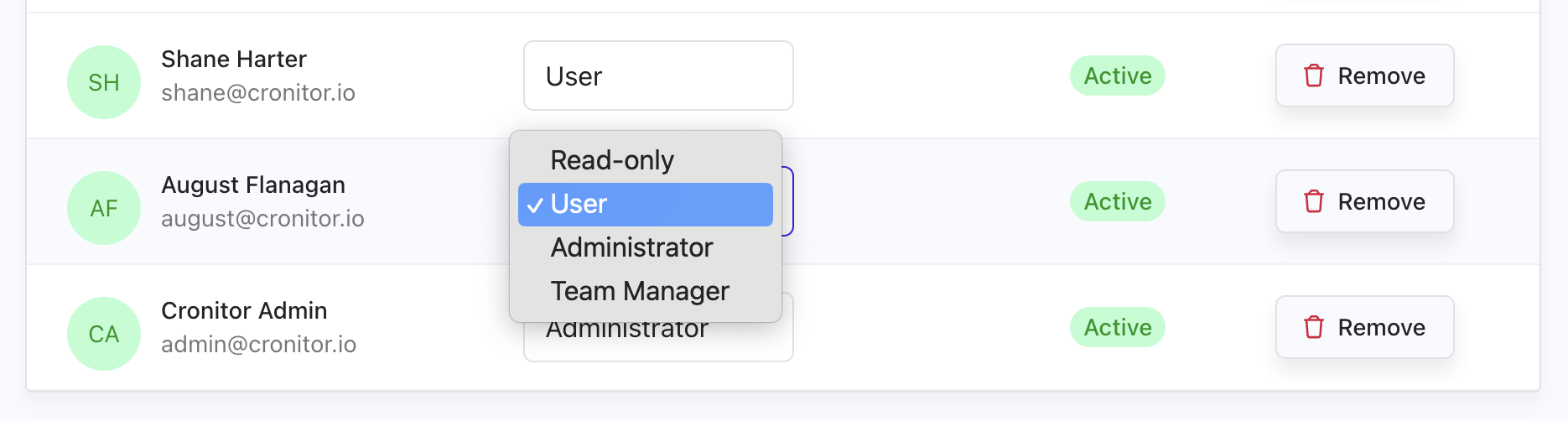
You can update any team member's role at any time:
- Find the user in your Team Settings
- Click the role dropdown next to their name
- Select their new role
- Changes take effect immediately
Important: Users will immediately gain or lose access based on their new role. API keys they've created will also inherit the new permissions.
Removing Team Members
Removing Team Members
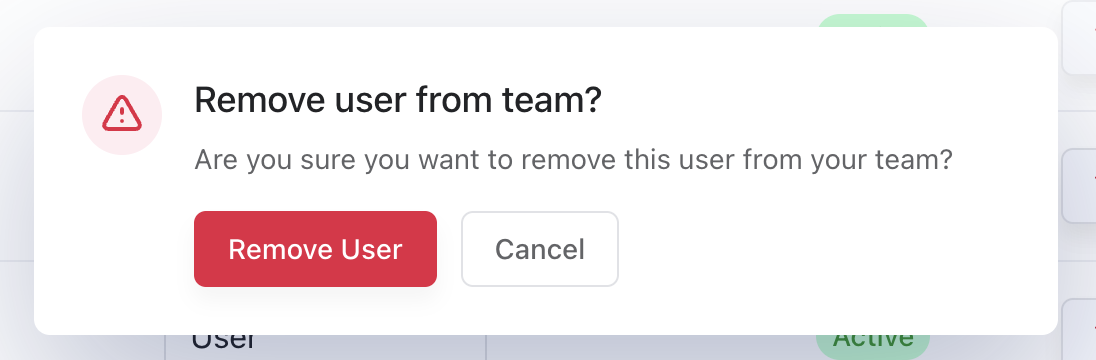
To remove someone from your team:
- Find the user in your Team Settings
- Click the "Remove" button next to their name
- Confirm the removal
Removed users will lose access to your organization immediately.
Authentication Options
Cronitor supports multiple authentication methods to fit your organization's security requirements:
| Method | Description |
|---|---|
| Email & Password | Standard login for accessing the web dashboard and creating accounts |
| SAML SSO | Enterprise single sign-on for web dashboard access with automatic user provisioning |
| API Keys | Programmatic access for API calls, integrations, and automated systems |